By, Media2Rise
Your personal data is very valuable. It is no wonder that hackers, governments, and corporations are trying to collect and catalog everything about you. Your search quires, your entertainment choices, your web history, online chats, and posts all paint a very detailed picture about who you are. Would you be comfortable sharing 100% of your online history with even the closest people to you in your life? Probably not – so why would you want to share it with people who have financial incentives to exploit all of your personal data and have access to it? There is a solution to stop the tracking though. And that is to take matters into your own hands and start protecting your data by changing your habits and using the correct software to enhance your privacy and anonymity.

Lets get one thing out of the way immediately. These steps I’m going to tell you are going to add a bit of a challenge to your computer and browsing habits. The web is designed in such a way as to not be private, combine that with a life of people being conditioned to trade off their privacy for convenience and you have the bulk of people relying on services such as google that heavily mine your data. In this article I’m going to start you down the right path to enhancing your privacy and security but it’s going to make things a bit more complicated as it requires a few more steps.
The first thing we will discuss is decentralizing your online accounts. Most people are using a single non-privacy respecting email (Gmail, Yahoo, Outlook, Hotmail, AOL, etc.) to sign up for everything from Netflix to Spotify, Grubhub, Uber, Amazon, etc. and what’s worse is they will oftentimes use the same password across all of these accounts including the email login. Just by doing this there is so much of your information that is going to be concentrated within that single email address! Especially, if you’re also using it as your primary email for correspondence. And if you’re reusing passwords any one of the services that are connected to it has a data breach that releases that password then your email and password will become available to that hacker and then they have access to everything and vice versa if the email service itself has a breach then all of the accounts that are connected to it become vulnerable to hacking. The most simple way to prevent this issue is to use a password manager along with multiple different email addresses. Way your all of your accounts won’t get hacked if one of your accounts happens to have a security breach. Also, your services cannot be personally linked to one another. This is one of the ways a dox might happen. Where one account that might be anonymous is linked to an account with personal information. For securing your passwords I recommend using KeePassXC or GNU password manager. Its best to avoid any password manager solution that asks you to pay money or does an online registration and syncing of your data to their cloud as that would compromise the anonymity of it. Unless you use Tor and a burner email to sign up for it then it’s going to be a little bit safer than just using clear-net and an email that is connected to your identity. However, again I suggest simply using an offline password manager since any password manager that needs an internet connection to work may be vulnerable to any type of eavesdropping that may happen when data from your computer is sent between it and a server. Of course, it’s also worth mentioning the (((Richard Stallman))) approach to password management and that’s to simply keep your passwords written down somewhere and keeping your damn mouth shut about it. As he would say,” You can’t hack pen and paper.” A Jew, but good advice nonetheless.
Now, when thinking through all of these things one important thing to keep in mind when securing your online activity is to create a “threat model”. This is simply a cyber security term used to by professionals when strategizing how to identify and defend a system from cyber threats. The process includes identifying defense mechanisms or weaknesses in a system and then provide the necessary mitigation. The most important part and the one we will be focusing on in this article is who and what you are actually going to be securing your data from. I must preface this by saying not to use this as your only source of legal advice but if your threat model includes law enforcement then you should take the additional step of not using any biometrics to secure any of your data or devices because fingerprints, face scans, and iris scans can be forcefully taken from you to unlock your data and unlock your devices. While passwords cannot unless of course you willingly give them up (that is unless you are subjugated to enhanced interrogation techniques) Again, this is not legal advice and I urge you to check local court cases where judges made rulings, such as the San Bernadino case. In general, European citizens have much more protection from these things than those in Asia or the Americas. So in addition to not using biometrics, an LE or government threat model should include having two-factor authentication for your hardware, for example a YubiKey for example. There are some downsides to using a hardware security key, if this key were to become lost or damaged all of your accounts that are connected to it would become inaccessible. Still, if the glow boys ever come knocking at your you can simply destroy your YubiKey Hillary Clinton style with a hammer and then all of those accounts would be inaccessible.
Next up we’re going to talk about real-time communication. For that there are a few options but this is where some additional work needs to be done for messaging. You will want to avoid SMS (short message service) at all costs. The detested green bubbles on an iPhone would be an example of an SMS conversation. These communications are not encrypted at all, meaning that they can be intercepted in plain text by cellular carriers, governments, or any hackers that decide to eavesdrop. In order to avoid SMS being used, both parties have to use the same kind of service that supports end-to-end encryption. This is where the toughest part is going to come in because obviously you’re going to need to get your normie friends, any family who still talks to you, or whoever you want to communicate with to use one of these services that they’ve probably never heard of such as Signal, Telegram, Element, Threema, Dust, and so on. These services generally aren’t advertised very much unless they follow Elon Musk on twitter. In general, it’s going to be a little bit tough to get normies to use them but they’re not terribly difficult to use. If you’re savy and have some experience with the aforementioned you’ll probably notice that the more secure the messenger is the less features it has. The easiest ones for n00bs are probably going to be Telegram or Signal. Remember Telegram does not do end-to-end encryption in its chats by default, that must be enabled. Signal is also an open source messenger that features end-to-end encryption with voice as well as video calling. It’s pretty easy to use but there are a handful of disadvantages to Signal. First, it’s still a centralized service. What this means is that its going to be more susceptible to backdoor access by any governments. Second, Signal’s ownership of the service could also very easily change into the hands of someone who doesn’t really care so much about the end user’s privacy. If a company getting into the hands of some non-privacy respecting entities is a major concern then I recommend that you use and convince your certified non-normie friends to use a federated service like Element or use a peer-to-peer solution such as Briar or Jami. Some more examples of federated privacy respecting social media platforms are Pleroma and Mastadon. I’ll be honest, they’re mostly platforms for nerds and weebs. That is, if you’re a verified oldfag then I don’t need to explain to you what type of political influence nerds and weebs on anonymous message boards have. Anyways, look out for those names in the news in the next couple of years when they start talking about censorship on Facebook and Twitter and what to do about it. Trust me, that problem has been solved but first thing you need to get off all social media now!
Finally, we want to secure your main gateway to the sewer that is the modern internet, the desktop web browser. Browsers nowadays are just another tool in the toolbox of big data used to collect information from people. It’s necessary to always use one with good security settings out of the gate as well as have the ability to configure these options further in order to harden it against potential data leaks and trackers. Using a browser like Google Chrome, created by a company that’s main cash cow is tracking and creating profiles on their users, is obviously not going to be privacy respecting out of the box. There will also be hidden settings to make sure you are still being tracked that you the user either can’t easily delete or cannot disable at all. The best option is to start with a spyware free browser that meets all these requirements without having to go in and change configuration settings. With the absolute fall from grace of Firefox I can no longer recommend any software by Mozilla. The company has a histroy of cancel culture when in 2014, the former CEO of Mozilla, Brendan Eich was deplatformed and pushed out for making a political donation to the wrong side of proposition 8 in California, a proposition to end same-sex marriage. Wow, based? If you are already a Firefox user and are looking for a similar alternative I recommend GNU IceCat or Libre Wolf. Now, if you do decide to use this option you will have limited access to sites that heavily rely on JavaScript. That means commonly used services such as YouTube won’t work the way they are supposed to. There are some workarounds to this like MPV player + youtube-dl. Don’t be fooled by the “youtube” in “youtube-dl”. This program also supports a bunch of video streaming websites. That way you won’t have to come up with a new solution for each place you want to consoom content. I won’t go into specific details about how to download, install, and operate these types of services. Obviously without a YouTube front end in your browser you’re not going to be able to comment or leave a like or anything like that but if you miss the Youtube front end in your browser you can use invidio.us. Lets say you’re a content creator and you need to interact with your YouTube account, you’re going to want to sign in from a different browser profile or a different browser altogether. This is because the best way to access certain services that you know are not privacy respecting is to compartmentalize your online behavior between different browsers, software, or computers altogether. Not convenient but still a good way to make sure anything you want to stay private stays private and anything you don’t mind sharing isn’t interrupted by stricter security measures. One other thing worth noting about these techniques is that they are usually lighter on your system resources than just watching a video in your browser directly. Videos are not actually being downloaded or saved, only streaming. There’s not going to be any privacy concerns or storage space concerns there either. For an easier to use browser that still has good security settings I would recommend using Chromium however you’re going to want to change some of your security settings for certain things you don’t want to store like cookies. You want to just delete those after Chromium is closed. Autofill addresses, credit cards, browser history, bookmarks, or anything else like that are other things you don’t want saved. With whatever browser you decide to use you will want to disable WebRTC, geolocation, and unique fingerprinting. One of the basics is to also install an ad blocker like uBlock Origin. With uBlock you can selectively disable JavaScript on sites because basically all of the ads that are displayed to you those are all driven by JavaScript. Did I mention how much I hate JavaScript and how it’s completely breaking the internet? I digress. With GNU IceCat it disables JavaScript by default and you’re not going to see any JavaScript adds at all, but like I mentioned early that will break many websites. Using uBlock, you can disable JavaScript from the advanced user settings. What that does is it will show you individual scripts that are getting loaded on a website and allow you to pick the ones you want and don’t want to run. Usually, I globally disable third-party Java scripts so it automatically blocks them. Then whenever you load another site it’s going to show other domains that you want to block scripts from. One downside is that if you’re on a site with really heavy ads cough cough streaming anime cough cough this is going to be really really tedious. You can go through and blacklist as many sites as possible or just as many domains that are showing scripts until you get whatever site you’re browsing to a point where it’s still functional but it’s just not showing anything additional that isn’t necessary for the site to actually work. You’ll also want to use the decentralized add-on for local content delivery network emulation so this is going to block unnecessary connections to CNDSs like Cloudflare and Google. This can also speed up the loading time of some pages by loading the relevant web libraries locally on your physical machine.
While we’re still on the topic of browsers its important to mention you should also avoid using search engines that are built to track your online activity across the web. Yes this means that Google and Bing should not be used for your search queries moving forward. At least not within the same privacy browsing profile. This doesn’t mean you can never use these searches, just use them sparingly and definitely not for anything that could be considered remotely dissident. Instead, you should be using services like (((DuckDuckGo))) owned and operated by a Jew which is probably the best Google alternative with a good track record. At the least it’s not connected to Google’s add engine nor does it manipulate search results. If you really wish to be the search engine dissident you can use start page to emulate google results in a more private way. For even better search privacy the search engine I’d recommend most is Searx as it is the most open (not open source) and transparent search engine that is currently available on the web. In reality you’re simply going to want to implement the use of multiple profiles within the browser for different use cases since even if you’re using a more privacy focused search engine other web pages you may have open can track your search results and target you adds. Maybe you still want to browse normie YouTube from time to time and leave comments, likes, and subscribes to your favorite content creators page. Its helpful maybe even for uploading videos if you’re a content creator yourself. Tl;dr if you just want to view other random things that you know you aren’t going to need a profile for to interact with it’s best to just browse to those pages from another browser profile altogether where you aren’t signed into your social media accounts. This will prevent those sites from tracking your watch history within the accounts themselves because of course they ultimately control the account they let you have for free. I’m sure you’ve heard this before but anytime there’s a service where something is free chances are you are the product.
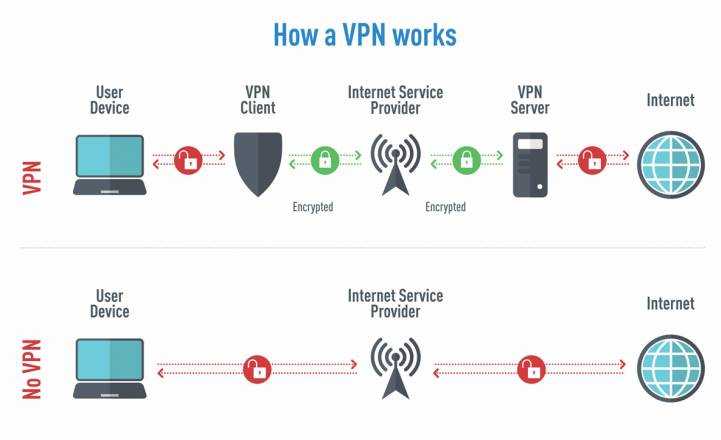
Before continuing this article I’d like to thank our sponsor Nord VPN – just kidding but this is the part where we discuss virtual private networks (VPNs). You can take your internet privacy a step further by purchasing a VPN and compartmentalize your online behavior to specific servers with specific browser profiles. This is good for preventing your ISP from tracking your different activities to your IP address that they give you. If you’re careful enough, the same could also go for any government agencies that want to subpoena your ISP for your browsing records. Keep in mind a VPN does not make you anonymous on the internet. All it does is shift the burden of privacy from your internet service provider to the VPN provider of your choice and for this reason alone it is very important to pick a provider that is as secure and anonymous as possible. With these requirements the only VPN that I can in good faith recommend is Mulvad. As far as I know they are the only one that is totally log free, meaning that they don’t really store any history of what you’re doing on their servers. Nor could I find any information at the time of writing this article about them selling user data. Most importantly is they also have a pay-by-cash option as well as the ability to create an account without giving up any user details. You have to be very mindful though if you’re going to go to this extreme in regards to privacy to NOT TO MIX YOUR CLEARNET ACCOUNTS. Meaning accounts that you created on your own IP address that your ISP gives you and your VPN accounts. An example would be if you created an account from your real IP address (lets say your work email) and then logged into it while when you’re connected to your VPN then those login details are going to be collected by the owner of whatever service the account belongs to. Take Facebook, for example, the time of day and the IP is going to be collected and now your real IP address and personal information that is connected to that account can then be connected to the IP addresses you connect to using your VPN. All it takes is one server because like Mulvad, Facebook offers you hundreds of different servers to connect to based on what’s going to give you the fasted browsing experience with different IP addresses but you can figure out who an IP address belongs to fairly easily. You know you can even tell what ISP somebody is using, you can also tell whether it belongs to a VPN. This is how websites are able to ban entire IP ranges. If somebody decides to abuse a websites platform over and over again then they’ll ban the entire range of whatever VPN service they’re using or ISP they’re using. The same thing works in reverse for tracking you down and identifying you. All it takes is one slip up, one server that gets connected to an account made with your real IP address and then the whole thing is essentially compromised. They can say, “Hey you know we know that this guy also uses Mulvad. We know that for a fact even though he paid in cash and he created it in an anonymous way without giving up any of his user details.” But as long as you avoid that and you create the VPN account in an anonymous way, meaning that you do it over Tor and you mail in a cash payment option for your account then you’re going to be good. For situations where you truly need to browse anonymously you should resort to using Tor, but again just because you’re using Tor doesn’t mean you’re completely anonymous. You should also block JavaScript again, as this can be used to reach through the three proxy hops of the Tor network and grab your real IP address as well as hardware info about the computer that you’re using which could uniquely identify you. Also, don’t use any accounts that are created on your public IP address, especially the ones with your personal identifiable information because you’ve got the same problem as using it with your VPN. Those accounts they can easily link your personal information to the Tor IP address that’s in use at the time and then track all of the activity back to you. Even things that go outside of that particular network like say you were dumb enough to sign into your Gmail over Tor and then you go do a bunch of other stuff with that same IP address. You’re the only person in the world that is probably using that IP address at that specific time. These are the ways your browsing data can be narrowed down to you, especially because there’s not that many Tor users out there. Another thing you could do to increase the effectiveness of the Tor network itself is to spread this information! Let other people in your circles know about it. The more people that are actually using the Tor network the more difficult it is for any one person to be identified on it. If I haven’t driven this point home hard enough, you should really just avoid online services that try to track you in the first place. Google, Facebook, Twitter they’re all designed to track you. Every mainstream social media platform is purposefully designed to track you. It’s very difficult to actually create and use these accounts especially when they require a phone number just to verify the account during sign up. Obviously, your personal phone number is going to be out of the question for a private social media account. If you all are interested in finding out how to create these accounts anonymously that require phone verification the process to do so is a little convoluted. To really do it correctly, it’s likely going to require a lengthy tutorial on its own.
There’s also much more to be taken into account to really protect your online security like securing your home wi-fi, securing your computers, your smartphones, and also how to just surf the internet without really revealing your identity. There are plenty of lengthy books, online tutorials, and classes all dedicated to the topic. This was meant to be an informative write-up to get you interested and researching these things on your own. Each person’s needs will be different and instead of trying to tell someone “you must do this or you must do that” it’s better to explain what’s out there, how it works, and why you may need it. The rest of the puzzle is up to you to solve, but when you do it correctly on your own it’s much more rewarding than paying someone else to do it or letting someone else decide what is best for you. Remember, you don’t have to start out with the devices you currently own – used cellphones and laptops to mess around with are cheap. As long as you aren’t storing important personal information on them the worst thing that can happens is you brick them. Learning to un-brick a phone or computer is also a rewarding skill to have. Another little tip is to think of online security like training form for lifting, the more you do it the more natural it becomes. Once you are finally confident in your skills you can start switching over to your “secure phone” or your “secure laptop” as your daily drivers. In the future, I may set up a way for you dear reader to get in contact in order to submit Q&As.


0 comments on “online privacy guide” Add yours →